Recently, Tencent Security Xuanwu Lab and researchers from Zhejiang University published a paper revealing a new fingerprint attack method that can bypass biometric authentication on Android smartphones.
“BrutePrint”, the $15 Attacking Method
This attack method, known as “BrutePrint,” exploits two zero-day vulnerabilities and design flaws in fingerprint sensors. It involves continuously submitting fingerprint images until a match is found with the user’s registered fingerprint, thereby unlocking the phone.
According to the paper, the BrutePrint attack requires physical access to the target phone and the use of a device costing around $15. The device communicates with the fingerprint sensor through the Serial Peripheral Interface (SPI).
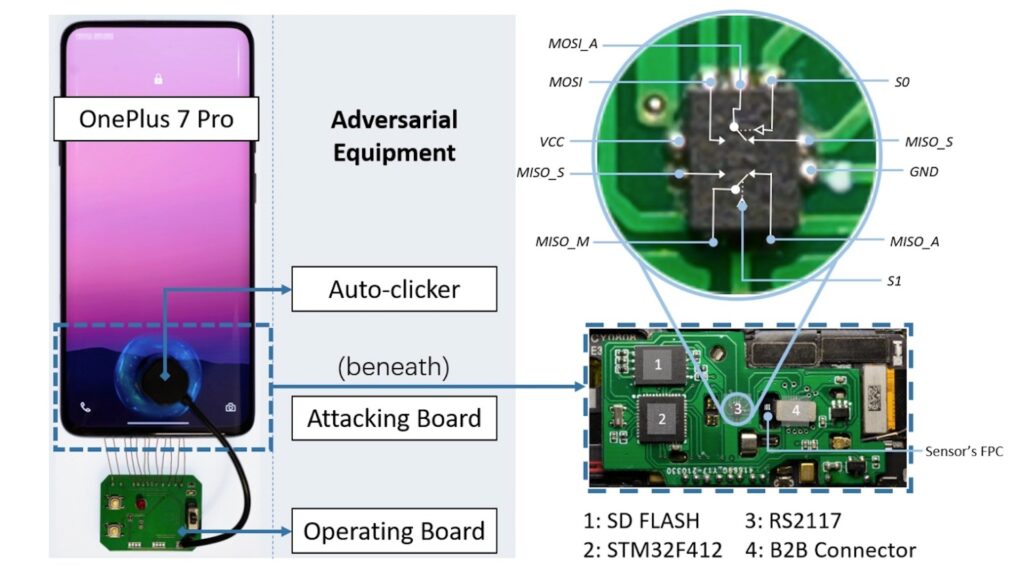
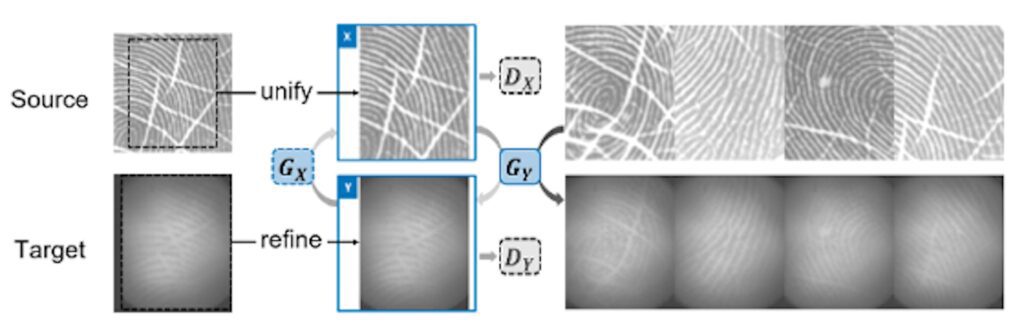
The attacker also needs to obtain fingerprint images from a publicly available fingerprint database and convert them to a format suitable for the target phone’s sensor using neural style transfer techniques. By doing so, the attacker can continuously attempt to submit different fingerprint images until a successful match is achieved. The report pointed out that the fingerprint lock can be cracked according to this process:
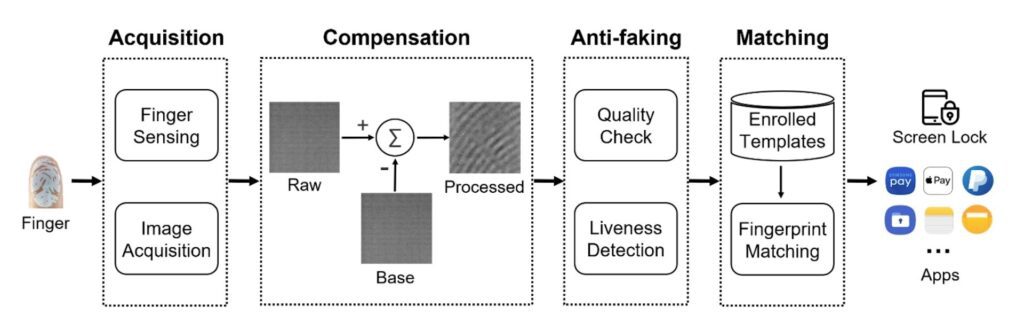
Bypass Android’s Limitations On The Number of Fingerprint Attempts
The researchers also discovered two zero-day vulnerabilities called Cancel-After-Match-Fail (CAMF) and Match-After-Lock (MAL), which can bypass Android’s limitations on the number of fingerprint attempts.
The CAMF vulnerability allows attackers to cancel operations after each failed submission, thus preventing the counter from increasing. The MAL vulnerability allows attackers to continue submitting fingerprint images even after the phone is locked.
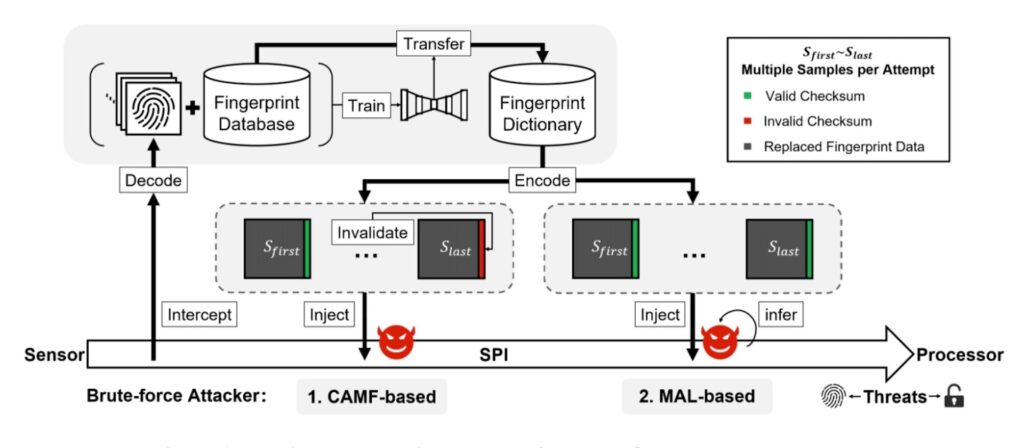
Fingerprint images are able to be submitted after the phone is locked.
Variety of Android Mobile Phones and iOS Mobile Phones were Tested
The researchers tested ten different brands and models of smartphones, and found that all Android and Huawei HarmonyOS devices are at risk of BrutePrint attacks, while iOS devices offer a certain degree of protection.
The experimental results showed that with only one registered fingerprint, the BrutePrint attack took between 2.9 and 13.9 hours to succeed, while with multiple registered fingerprints, the time required was reduced to 0.66 to 2.78 hours.
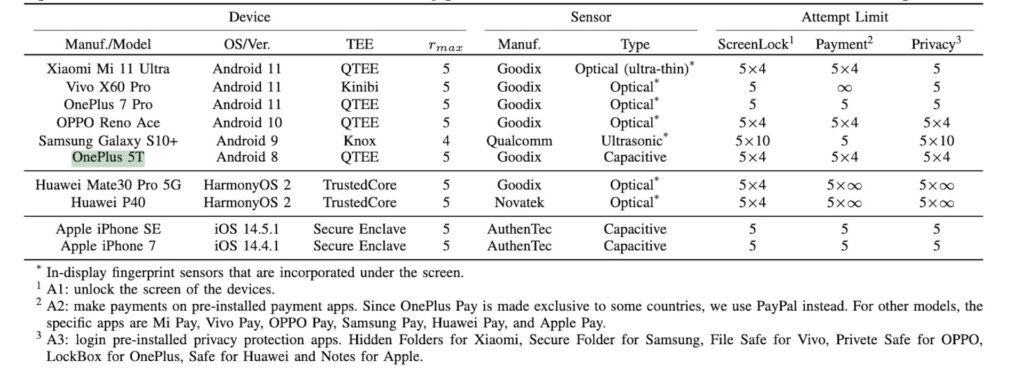
Test result:
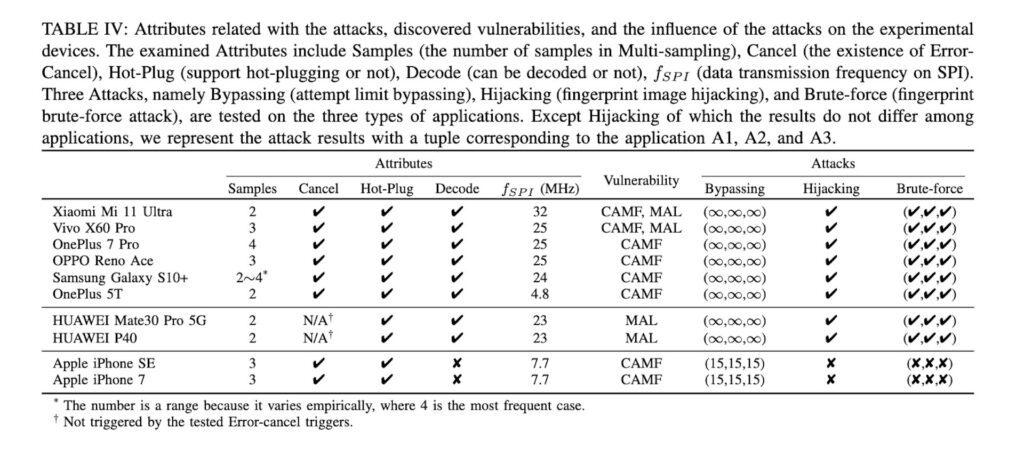
The fastest success results lies within 1 hour
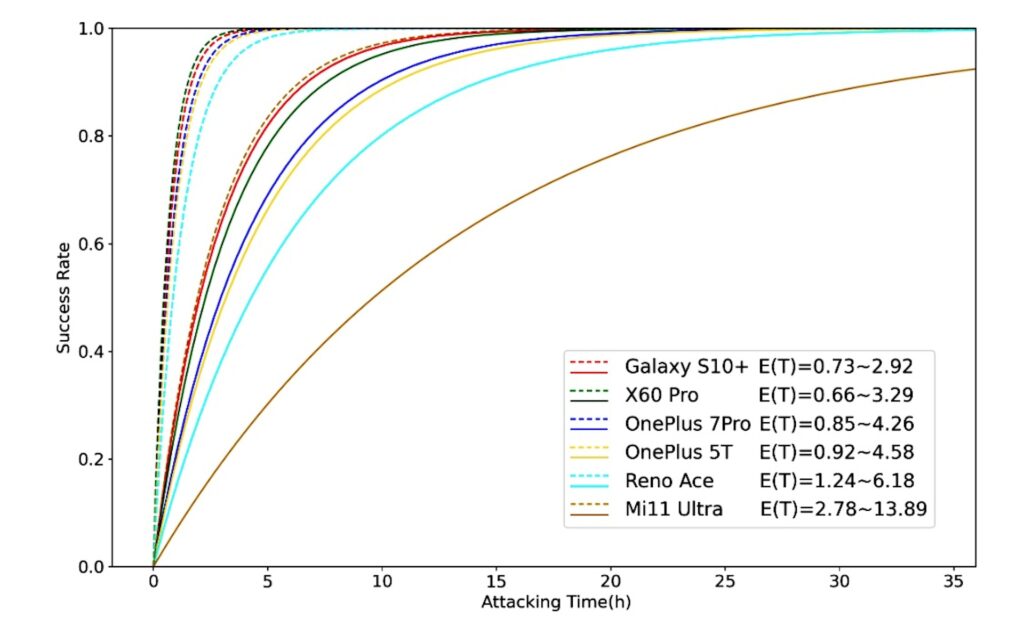
The researchers have reported these vulnerabilities to the relevant manufacturers and recommend that users utilize more secure methods of authentication, such as passwords or facial recognition. They also urge manufacturers to improve the design and protective mechanisms of fingerprint sensors to prevent similar attacks from occurring.


